While monitoring the 6 MHz band looking for the 48KBd "monster", I ran into some STANAG-4538 "circuit mode service" transmissions on 6898 KHz/USB using the 110A Serial Tone in 2400bps/S mode as traffic waveform: likely US Military. The bitstream after 110A removal (Figure 1) clearly shows the use of encrypted frames which are characterized by 256-bit length Initialization Vectors (IVs), the underlying data-link protocol is then blacked.
 |
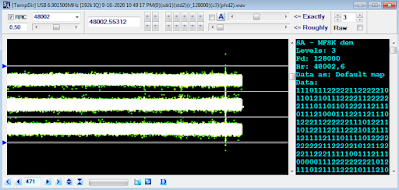
| Fig. 1 - demodulated bitstream |
The transmission frames structure (Figure 2) is very interesting and - in some way - it reminds the embedded COMSEC frame structure as per MIL-STD 188-110D App.D; in this case (the recorded samples) the COMSEC preamble should consist of five components:
b) 226-bit sequence (frame sync?)
0101101111011010010000100011110110111101110000100100001111000100
0101110110100011101001011011101111011100001001000011110001000101
1100001000111010010110111011110111000010010000111100010110100010
0100001110111101101000100011110101
c) 8 x 256-bit (32 bytes) Initialization Vectors (a same IV is repeated eight times)
d) 350-bit string of alternating ones and zeros (bit-sync/phasing?)
0101010101010101010101010101010101010101010101010101010101010101
0101010101010101010101010101010101010101010101010101010101010101
0101010101010101010101010101010101010101010101010101010101010101
0101010101010101010101010101010101010101010101010101010101010101
0101010101010101010101010101010101010101010101010101010101010101
010101010101010101010101010101
e) 150-bit sequence (frame sync?)
0110001011010001111000010010000111011110111011010010111000100001
1101000100011110000100100001110111101110110100101110001011011101
0001000111100001001000
Encrypted data block follows, ended by the 40-bit sequence: 0000010010110110010110100101101100100000 (probably acting as EOM).
 |
| Fig. 2 - transmission frame structure |
Interestingly, the sequences b) and e) have a period length of 60 bits and each sequence may be descrambled by the polynomial x^3+x^2+x+1.
About the initialization vectors (Figure 3), it's to notice that a 16-bit segment (positions 113-128, as if they consist of two 128-bit blocks) has the same value in all the four vectors, but
it could be just a mere coincidence and thus futher samples are needed. Anyway, it's the first time I meet 256-bit length initialization vectors: since their size is as large as the block size of the chiper in use (or as large as the encryption key) it is probably a 256-bit encryption system. In this regard, I only know about "HC-256", a software stream cipher for embedded systems which generates keystream from a 256-bit secret key and a 256-bit initialization vector [1], but this is still speculative.
Since 110A was using a data rate of 2400 bps, the time needed to send a complete IV sequence (2048 bits long) is about 853 msec.
| Fig. 3 - four initialization vectors |
Recordings were made thanks to KC9FFV Marco who run a KiwiSDR at Forney, TX USA [2].
https://yadi.sk/d/43XB38wq1R6Pkw
[1] https://www.ecrypt.eu.org/stream/ciphers/hc256/hc256.pdf
[2] http://marcocam.selfip.com:8073/