This is an interesting "Akula-like" FSK waveform spotted by my friend cryptomaster on 7370 KHz/usb (41 mt broadcast band!), the signals are keyed at the speed of 500 Baud with frequency spacing of 1000 Hz. The recorded session consists of messages (the longer segments) followed by short ACKs which are sent back from apparently two correspondents; ACKs partially overlap each other and sometimes they seem even superimposed (figure 1).
 |
| Fig. 1 - FSK 500Bd/1000 |
 |
| Fig. 2 - raw and differential decoded signal |
After differential decoding, I found consistent matches for the scrambler described by the polynomial x^12+x^10+x^9+x^3+1 (or its equivalent x^12+x^9+x^3+x^2+1): after its removal, a common "area" of (at least) 253 bits emerges immediately after reversals (figure 3): most likely that's the preamble section which therefore consists of a 253-bit pseudo-random sequence (PRBS) which is part of the 4096 bit M-sequence generated by the aforementioned polynomial.
 |
| Fig. 3 |
Removing the initial reversals from the differential decoded bitstreams, we are able to get and analyze either the data blocks and the preamble sequences: as expected, the latters are the same (figure 4).
 |
| Fig. 4 - 253-bit pseudo-random sequence used in the sent messages |
The data blocks are even-parity checked (figure 5) and consist of 24-bit codewords each consisting of 23-bit length data sequence followed by one parity bit. Since the use of a single parity bit can't correct any error, my idea is that they could use a kind of (24,k) code with 24-k parity bits (EDAC bits). The identification of which particular code is used is not easy, it must be taken into account that the parity bits maybe dispersed in the codeword and the possible use of the bit-inversion technique as well as the order in which data and EDAC bits are arranged into the codewords.
 | |
| Fig. 5 |
Looking at figure 7, the variation of the length of the initial bit reversals (260 and 980 ms) of both message and ‘ACK’ packets suggest that the messages are sent by separate modems. Indeed, listening to the recording it is obvious, that (at least) three different stations are present and that they seem to operate in half-duplex mode with one station at a time sending messages, and one or two stations responding, sometimes on top of each other.
Also notice in figure 7 the lack of ‘ACK’ after message B. This might indicate the deployment of a stop-and-wait ARQ mode, ie A packet is repeated until an acknowledgement is received. However, the decoded succeeding message C is not identical to message B.
 |
| Fig. 7 |
Please, also notice that the partial collisions of the ‘ACKs’ occur when the message transmitting modem is the one with a long run of bit reversals. Such a partial collision is much more evident in figure 8 where the existence of two slave modems can be clearly distinguished. This could indicate that this station is the master station of the network.
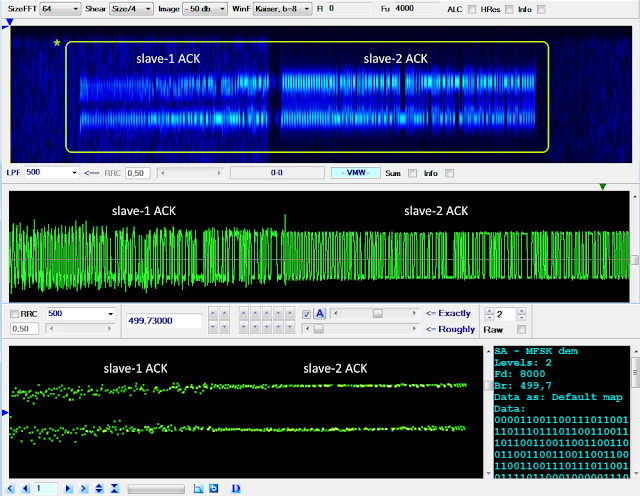 |
| Fig. 8 |
Due to the partial collisions, the shorter ‘ACKs’ as expected only exhibits part of the preamble sequence (figure 9):
 |
| Fig. 10 |
Differential demodulation in chronological order of the recorded ‘ACKs’, does not offer much additional information other than a very varied 48-bit format (see figure 11). In the figure the lengths of the data sections are unequal. That format is due to the fact, that I somewhat arbitrarily used the beginning of the trailing bit reversal ("01") sequence (if any) as a delimiter; there is no obvious evidence of parity bits nor of particular patterns. Bit reversals and preambles have been removed.
With a cautious approach, I could imagine three reasons for the collisions:



No comments:
Post a Comment