I56578, ANgazu
The Antarctica department of La Salle Campus, Ramon Llull University of Barcelona has been carrying out studies for some years, among which we are interested in the communications part. They study remote sensing IoT communications using NVIS platforms, a very useful system in places where there are no mobile communications infrastructures and the physical conditions do not invite useless movements. They are also studying HF links between Antarctica and Spain, of just over 12000 km. To allow the sending of the appropriate sensor data, since many bases remain closed or under minimum during the Antarctic winter. These tests include testing with various modulations to try to find the optimal one for the application.
Regarding the tests in Spain. they use an NVIS link between the Barcelona campus and the Cambrils campus. As far as we know, they do the tests at 5400 KHz, taking advantage of the University's Radioclub that collaborates with the department.
At present, we guess they continue with the tests and we assume that the recordings we are making correspond to them. The use of NVIS antennas limits the reception possibilities, since the Alicante KiwiSDR is not operational. However, with the available devices we are recording signals and we hope that some of them will meet the necessary quality for their analysis.
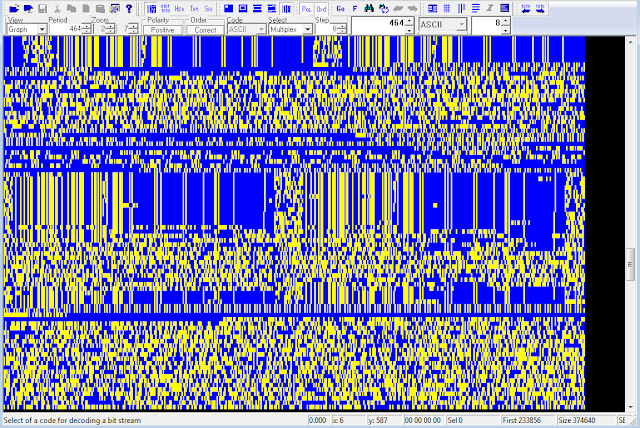
We can see in the spectrogram (figure 1) that they use a bandwidth of about 12 Khz, a bit excessive for the signal parameters.
 |
Fig. 1
|
The blocks are transmitted between 1 and several minutes apart. There does not seem to be a regular structure. Every block is made up of 25 segments, although there are some 14 and 50. Each segment measures about 265 ms, of which 60 correspond to a continuous carrier that is about 600 Hz. above the transmitter carrier.
 |
Fig. 2
|
The "current" framing of the segments is very different than the one described/used in 2018, see figures 3a-3b: its duration is 265ms and in my opinion the data part has a duration of 70ms and is followed by a 115ms (or better, 110ms + 5ms) pattern.
 |
Fig. 3a - current framing (the one we recently saw)
|
 |
| Fig. 3b - framing used in the tests carried out in 2018 |
Although there are some uncertainties and doubts in some segments the modulation used appears to be PSK4, but its analysis requires much more attention: at this regard I edited the signal and removed to 60ms tone as well as the ending 115ms segment (see figure 3a). Results are shown below, please note that the SA PSKn demodulator:
* does not lock on any sync sequence thus phase rotations are unavoidable
* it uses the following symbol mapping for PSK4 constellation:
0 (00) ==> 00°
1 (01) ==> 90°
2 (10) ==> 180°
3 (11) ==> -90°
Figures 4a-4b shows a standard PSK4 constellation with its regular and expected transitions between the four states, anyway figure 4c shows that the trajectories do not match the ones of PSK4 (figure 4d): ie, all the transitions are featured by zero-crossing paths like a π/2 rotated PSK2 (0<->180,90<->-90). Also note the slight "smudges" on the trajectories of figure 4c which led us to analyze the states by using a 8-ary constellation.
 |
Fig. 4
|
Actually, we don't know how much sense an 8-ary constellation makes, since the modulation clearly "dances" around four states, anyway it's interesting to see the π/4 rotation of the transitions shown in figure 5b as verified by the trajectories shown in figures 5c,5d.
 |
Fig. 5
|
That said, we demodulated the blocks using PSK4 demodulator and the mapping shown above: the resulting bitstream is about 914 bit (457 dibit symbols) which is compatible with duration & speed (205ms @2380Bd) of the bursts. At glance, it seems that each segment of a block transports the same data (figure 6).
 |
Fig. 6
|
That's all at the moment, further recordings and analysis are obviously needed and hopefully some confirmation from the testers. Comments and tips are very welcome.
https://disk.yandex.com/d/qmm7aDnwWshq0w