Prompted by some logs posted on the UDXF group, I started monitoring the USB frequency 12354.4 KHz, operated by the Tunisian Navy (Marine Nationale Tunisienne), hoping to capture something interesting. To be precise, I used the two KiwiSDRs located in central-eastern Italy, operated by IZ6BYY and IK7FMO [1], whom I obviously thank.
The frequency is quite "busy" with 2G-ALE (MS-141) exchanges between tactical callsigns, as RF05 and CT12 in the given sample; once the link is established, message exchange usually occurs via MS-110A using adaptive speed and interleaver (Figure 1). Still in this sample, it is interesting to note that the request to establish a link is transmitted from RF05 (caller node) to CT12 (called node) and after the exchange of messages the link is closed by the called node, as if to signify that there are no other messages to send in the opposite direction (a bit like what happens in 3G-ALE).
 |
| Fig. 1 |
The bistream after demodulation of the three message blocks shows the characteristic 16 bytes start/sync sequence of the L3Harris "Citadel" cipher (Figure 2).
 |
| Fig. 2 - Citadel start/sync sequence in the MS-110A demodulated bitstream |
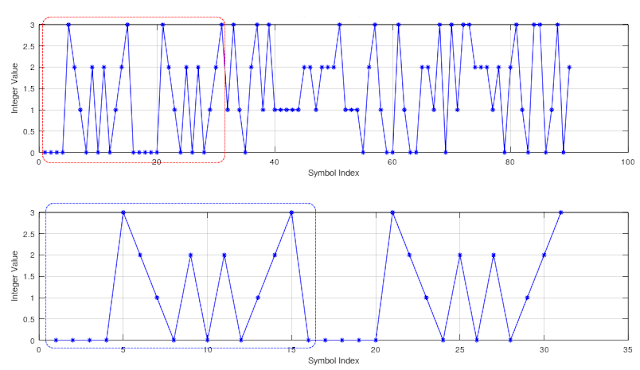
After removing the start/sync sequences, the presence of Initialization Vectors (IV) is noted: these are 16-byte/96-bit long, each repeated three times (Figure 3).
79 19 08 E9 61 C4 B1 01 A5 24 9A B7
87 A9 45 4F 28 22 A7 15 33 88 F8 EB
91 1E 71 15 D2 FA FF D3 51 68 6B D0
This is characteristic of the Citadel II "format":
- 16 bytes start/sync sequence 0x1E561E561E561E001A5D1A5D1A5D1A5D (Citadel)
- 12 bytes IV (each 3 times rptd) - OR - 32 bytes IV (2×128 bits parts, each 3 times rptd)
- ciphertext
- 8 bytes end sequence 0x1E561E561E561E08 (Citadel)
 |
| Fig. 3 - 12-bytes/96-bits Initialization Vectors |
Some comments
"Citadel II" generally refers to a hardware-based cryptographic solution (cryptographic engine) developed by Harris Corporation (now L3Harris) in 2004, designed for military-grade encryption in "non-Type 1" applications. This means it's approved for secure communications but not for the highest classification levels of US government information (which use "Type 1" ciphers endorsed by the NSA). One might wonder why this encryption is used by a country like Tunisia, which is notoriously not a member of NATO (1): the answer is because it is not a Type 1 device, the Citadel II is approved for export from the United States, making it available to international users.
Citadel II is used in various communication products, including the L3Harris Falcon II range of military radios (such as RF-5800H). Given L3Harris's extensive portfolio and the strong military ties between the US and Tunisia, it is highly probable that the Tunisian Army runs L3Harris equipment, particularly in areas like communications, night vision, and potentially some avionics or electronic systems on US-supplied platforms [2]. However, exact details of specific L3Harris models in Tunisian service are not always publicly disclosed.
The short duration makes one think of "informal messages", perhaps SMTP emails: the encryption unfortunately obscures the data-link protocol sitting at the upper layer, probably STANAG-5066. Considering the use of L3Harris encryption (and probably Falcon radios), one might think that the L3Harris' RF-67x0W Wireless Gateway/Message Terminal is used... but that's just my speculation!
https://disk.yandex.com/d/23rAAmgmk9AiAQ
(1) Since 2015, Tunisia has been granted non-NATO "major ally" status, a status granted by Washington to allied countries that have strategic relations with the American armed forces but are not members of the organization.
[1] https://iz6byy.k1fm.us/ http://ik7fmo.ddns.net:8073/
[2] https://adf-magazine.com/2025/04/tunisian-navy-adds-to-patrol-fleet/