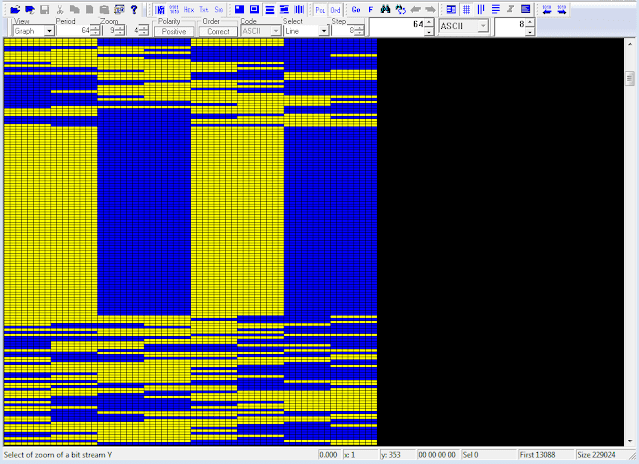
Recently I analyzed an interesting recording sent me by my friend Mike (mco) some days ago; for clarity, the transmission was recorded on 8006 KHz/USB. As shown in Figure 1, the recording consists of four data segment sent using the 188-110A Serial Tone (at 600bps/S), two 188-141B async call PDUs ("obsoleted", 3G-ALE)(1) and a final FLSU (Fast Link SetUp) PDU that terminates the link, the latter BW5 waveform suggests a STANAG-4538 3G-HF "circuit mode service" transmission, as well as the use of the 141B async call suggests the use of Harris equipments.
 |
| Fig. 1 |
 |
| Fig. 2 |
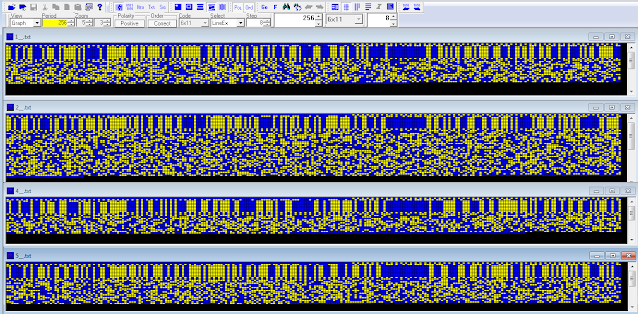
The frame structure appears almost the same of the one analyzed in a similar transmission analyzed some times ago [1], in that case the 110A modem was used at 2400 bps/S. Studying more closely the four bitstreams, it's possible to see recurrence of a same COMSEC preamble consisting of 01s sequences for bit phasing, same repeated sequences (probably for frame sync), and obviously the four different 256-bit length Initialization Vectors (Figure 3).
 |
| Fig. 3 |
223-bit sequence sync:
0101101111011010010000100011110110111101110000100100001111000100010111011010001110100101101110111
1011100001001000011110001000101110000100011101001011011101111011100001001000011110001011010001001
00001110111101101000100011110
256-bit Initialization Vectors, each 8 times repeated:
E7 F6 45 FD 63 53 2A 4B 91 0B 0E B7 A8 80 00 00
D7 32 3B 83 D0 6F 57 03 A9 65 CA F7 64 64 00 00
87 32 AA F0 9C 3D 03 EE E2 00 26 EF 45 4D 00 00
77 CD 93 E5 EB AF 65 3D B6 2B 1A 47 4E 19 00 00
phasing
32-bit sequence sync (6 times repeated):
8B 87 84 7B
The COMSEC preamble is followed by encryption, according to the standard MIL 188-220D [2].
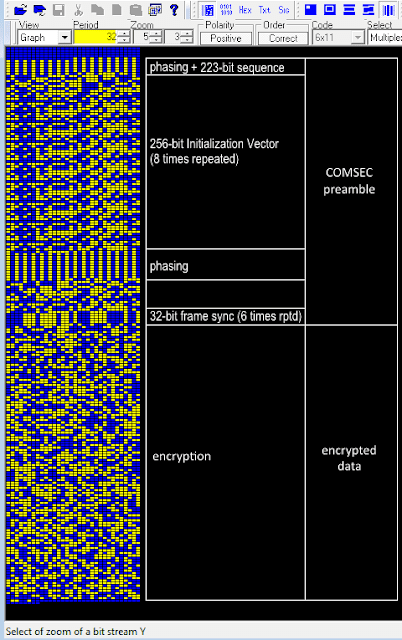 |
| Fig. 4 |
[1] https://i56578-swl.blogspot.com/2020/09/s-4538110a-transmissions-using-unid-256.html
[2] http://everyspec.com/MIL-STD/MIL-STD-0100-0299/MIL-STD-188-220D_CHG_NOTICE-1_24817/
[3] https://www.ecrypt.eu.org/stream/ciphers/hc256/hc256.pdf